On August 11, 2023, the NoEscape Ransomware gang claimed to have attacked auDA (au Domain Administration) and had stolen 15 GB of sensitive data that included:
- Powers of Attorney
- Legal documents with seals
- Passports
- Personal Data
- Medical Reports
- Loan Repayments
- Dismissal Documents
- Declarations
- Death Certificates
- Access to Customer Bank Accounts (name pw bsb acc)
- Taxes
- Much more confidential information
In an Official Statement on their website on Friday 18th August, 2023, auDA denied the breach and said “We have so far found no evidence of such a breach”.

This means, that for 7 days, auDA either had NO IDEA they had been hacked, OR, they were not telling the truth about being breached, OR, they weren’t hacked at all?
Either way, this is not a good look for a company who claims to be on top of their cybersecurity as they run Australia’s .au domain name system which the Australian government deems as “Critical Infrastructure”.

For people who know how to access “The Dark Web”, the NoEscape Ransomware information is publicly available.
During these 7 days when auDA claimed they either had NO IDEA they had been hacked, OR, they were not telling the truth about being breached, OR, weren’t hacked, the NoEscape Hackers claim they had been in contact with auDA about the breach, as currently stated on their Dark Web blog:

You will note that at the time of writing this post, auDA have 1 Day and 19 hours to “contact” NoEscape:

As of today, 21st August, 2023, auDA now admit that “the cyber criminal has provided evidence of a small sample of data” and auDA are “investigating”.
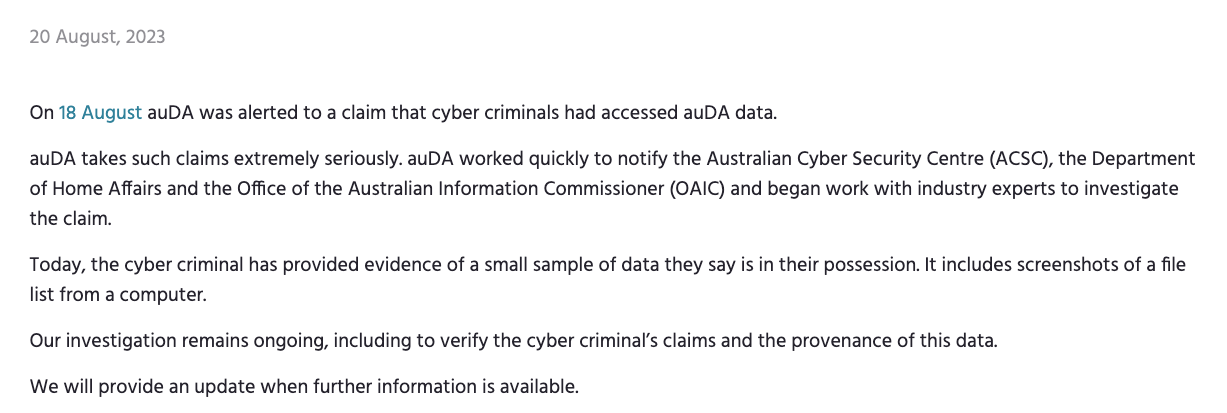
Does this mean auDA are admitting they have been hacked?
What’s also very interesting to note is that auDA claim to be ISO/IEC 27001 compliant as at 2020. However, the current standard for ISO 27001 appears to be ISO/IEC 27001:2022.
auDA has been pushing for all Registrars to become ISO27001 (even if it is not required in their public documents – see 15.1 Security obligations https://assets.auda.org.au/a/2020-11/auDA-Registrar-Agreement-20200625.pdf – https://www.auda.org.au/industry/information-registrars/registrar-accreditation).
A massive question now is…
How can auDA hold their Registrars to a standard (to safeguard the Registry Data, the EPP interface,
the Registry Connections, the WHOIS directory server, the DNS server infrastructure and the Registrar Systems, against any Security Breach.) that they themselves seem unable to attain?
Other questions are:
- Will auDA publicly admit they have been hacked? Have they? If so, when?
- Why did it take auDA 7 days to realise they had been hacked, if they had?
- Will auDA pay the NoEscape Ransomware demands?
- If auDA don’t pay, what sort of data and secrets will be publicly exposed when the download is released in 43 hours?
Story developing… Check back often and sign up to the mail list for latest updates.
DISCUSSION is happening here: LinkedIn and Twitter (X)
ITWIRE say:
UPDATE 01: (6pm AEST)
This is the latest update, according to MSN.com
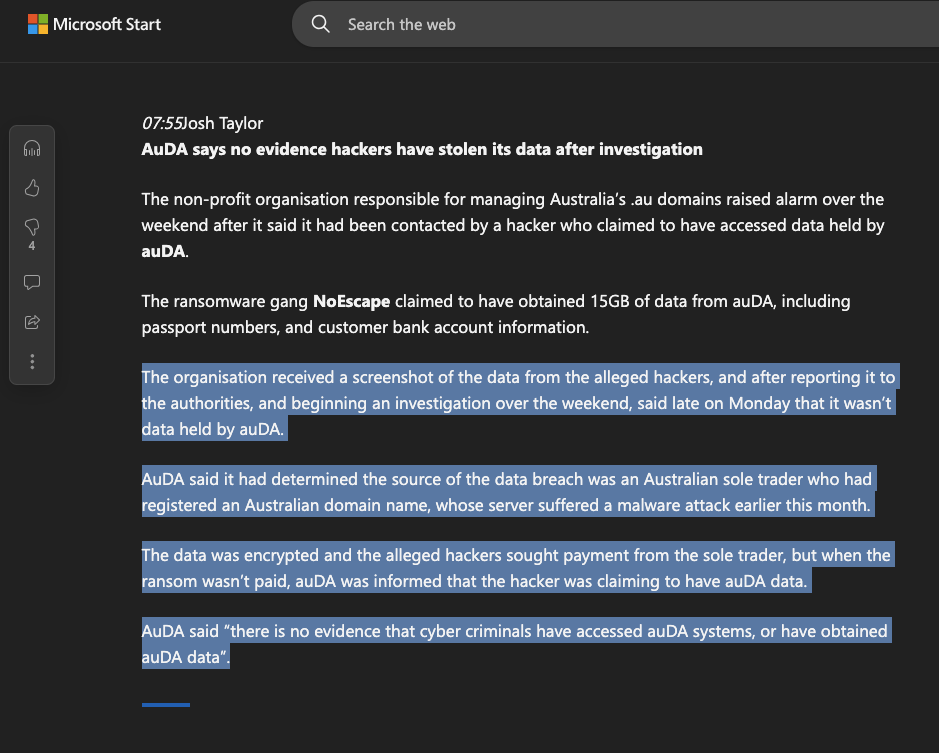
The organisation received a screenshot of the data from the alleged hackers, and after reporting it to the authorities, and beginning an investigation over the weekend, said late on Monday that it wasn’t data held by auDA.
AuDA said it had determined the source of the data breach was an Australian sole trader who had registered an Australian domain name, whose server suffered a malware attack earlier this month.
The data was encrypted and the alleged hackers sought payment from the sole trader, but when the ransom wasn’t paid, auDA was informed that the hacker was claiming to have auDA data.
AuDA said “there is no evidence that cyber criminals have accessed auDA systems, or have obtained auDA data”.
UPDATE 02: (6:40pm AEST) (https://www.auda.org.au/statement/resolution-cyber-incident)


